If you like me spend a lot of time in the swiss-army-knife of webservice development called SoapUI when not in Visual Studio or PowerPoint, you could end up getting bitten by this problem.
Java based SoapUI has great built-in support for both consuming webservices and exposing mockservices using 2-way SSL aka. two-way or mutual SSL. It is a proven and interoperable way to exchange data in B2B and enterprise scenarios in a secure way. It means that during the TLS/SSL handshake the client proves its identity to the server using a PKI challenge the same way as the server does to the client in normal TLS/SSL. To allow this the client needs a client certificate with a corresponding private key.
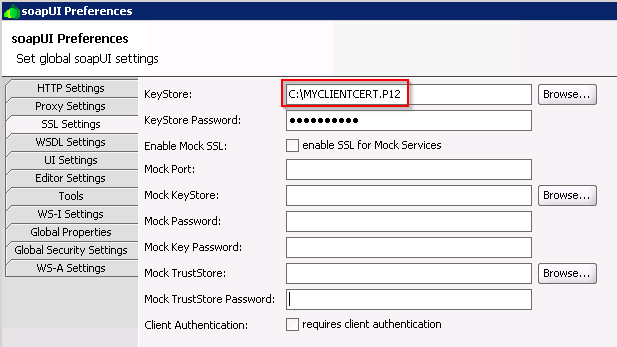
Doing most of my work in .NET i tend not to use the JKS (Java Key Store) that much and to call a webservice requiring certificate authentication in SoapUI i just point to a PKCS12 file directly. The PKCS12 file (.P12 or .PFX) are easy to move to and from the windows certificate store and is one of the standard containers for certificates with private keys.
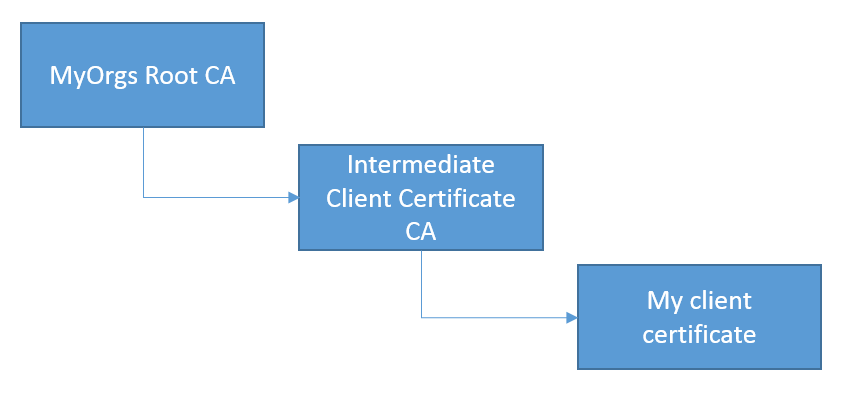
Normally this works perfect but if you are having trouble getting the SSL handshake to work one (of many) reason can be that the client certificate you are using has a trust chain including an intermediate CA which is getting more and more common.
The symptom is that SoapUI during the handshake simply wont participate in the client authentication thus leaving you with either a 403 or simmilar.
In .NET this normally just works as you most likely have the complete chain of trusted certificate issuers in the Windows Certificate Store. But in SoapUI and other Java clients you can no longer rely just on the P12 file.
To solve this for SoapUI and other Java applications you need to create a JKS file containing the full certificate chain under the same alias.
1. Convert the PKCS12 to a JKS using Javas keytool.exe utility. You can find the utility in Javas JRE\BIN folder. If not elsewhere you have this together with the SoapUI installation.
jre\bin\keytool.exe -importkeystore -srckeystore MYCLIENTCERT.P12 -destkeystore MYCLIENTCERT.JKS -srcstoretype PKCS12 -deststoretype JKS -deststorepass password -srcstorepass password -destalias my-client-cert-alias -srcalias "my client cert"
<p>
</p>
<p>
2. Then you need all public certificates in the chain including both root and intermediate CA cert. Export them from windows certificate store in Base64 format (.CER)
</p>
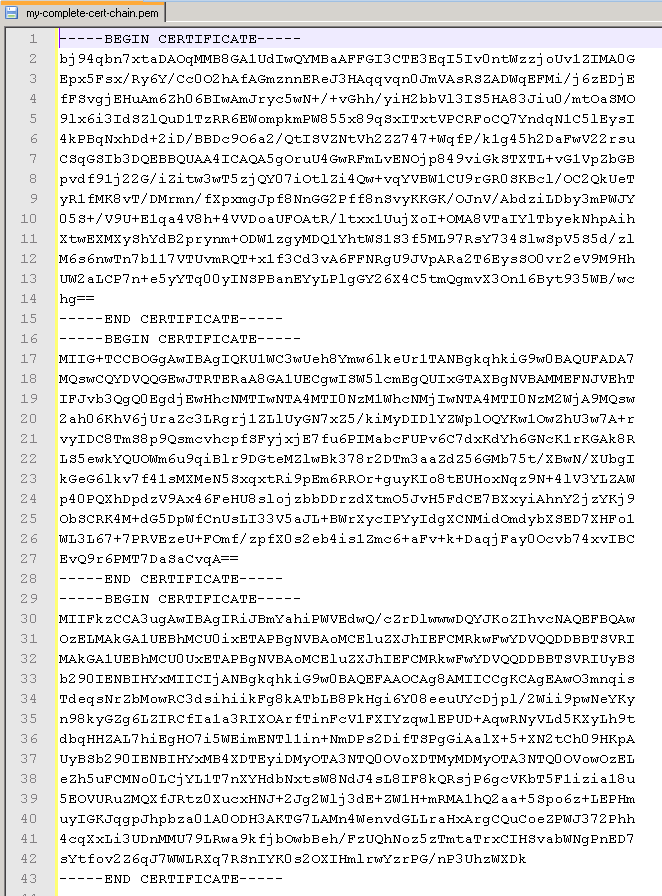
3. Open all three files in a texteditor and chain them like this:
Save the file as my-complete-cert-chain.pem
4. Import the file to the JKS using
jre\bin\keytool.exe -import -keystore MYCLIENTCERT.JKS -alias my-client-cert-alias -file my-complete-cert-chain.pem
<p>
</p>
Now you got a JKS with your client certificate certificate chain that should work fine in SoapUI or in other Java-based webservice clients. 🙂